secure your web application by setting up microsoft web application firewall on azure application gateway  Edit
Edit
In this article, we will learn about how to secure your web application by setting up a Microsoft web application firewall on the azure application gateway. WAF is the first line of defense between the app and the internet traffic. It monitors and filters internet traffic to stop bad traffic and malicious requests. Azure Web Application Firewall on Azure Application Gateway provides protection of your web applications from common exploits and vulnerabilities. WAF can protect applications hosted on Azure as well as those which are hosted on other clouds or on Premise. it makes your web application highly available and helps you meet compliance requirements.
There are three deployment options for Microsoft Web Application Firewall. The first one is Azure Web Application Firewall on Azure Front Door, the second option is Azure Web Application Firewall on Azure Application Gateway and the third option is WAF on Azure Content Delivery Network. Both Front Door and Application gateway provide various layer 7 load-balancing capabilities for your applications. The main difference between Front Door and Application gateway is Azure Application Gateway is a Regional Load Balancing Solution whereas Azure Front Door is a Global Load Balancing Solution & Azure Front Door does not work on VM / Container level. Front Door can load balance between your different scale units/clusters/stamp units across regions, Application Gateway allows you to load balance between your VMs/containers, etc. that is within the scale unit. Both of them can be Implemented With Web application firewall. In addition to HTTP, HTTPS, and HTTPS2 supported by Azure front Door Azure Application Gateway Support Websockets.
In this article, we will focus on Azure Web Application Firewall on Azure Front Door
What is Application Gateway?
An application gateway is a web traffic load balancer that enables you to manage traffic to your web applications. It is a highly available, scalable, and fully managed application delivery controller (ADC) service from Microsoft Azure. The main difference between an Azure Load Balancer and an Application gateway is that Load Balancer load-balances traffic at layer 4 (TCP or UDP) whereas Application Gateway is a layer 7 load balancer, which works only with web traffic (HTTP, HTTPS, WebSocket, and HTTP/2). You can use the same application gateway for up to 100 websites with multi-site hosting. Application Gateway includes TLS policy management and end-to-end TLS support.
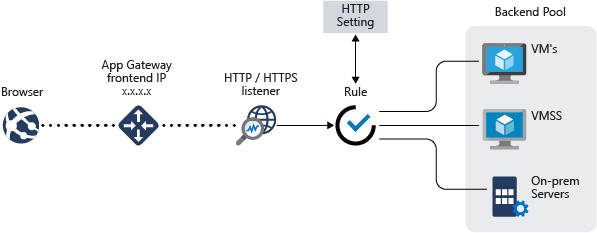
Application Gateway can do URL routing and more, for example, URI path or host headers. For example, if the incoming URL is /images then you can route the traffic to a specific set of servers, or if /video is in the URL, then the traffic can be routed to another set of servers. They can also make route decisions based on additional attributes of HTTP requests like host headers.
What is Web Application Firewall (WAF)?
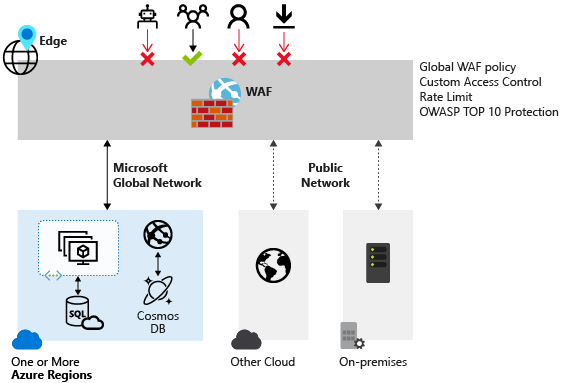
Web application firewall (WAF) protects your workload from common exploits like SQL injection attacks or cross-site scripting attacks, to name a few. Application security will not be complete without the mention of OWASP, The Open Web Application Security Project (OWASP) is a nonprofit foundation that works to improve the security of software. OWASP is globally recognized by developers as the first step towards more secure coding. The OWASP Top 10 is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications. WAF provides Protection for the top 10 Open Web Application Security Project (OWASP) security vulnerabilities This protection uses rules from the Open Web Application Security Project version 3.0 or 2.2.9. The WAF automatically updates to include protection against new vulnerabilities, with no additional configuration needed.
WAF can be Deploy in minutes & It provides customized rules to meet your web app security requirements. With WAF you can get Near real-time visibility and alerts through Azure Monitor.
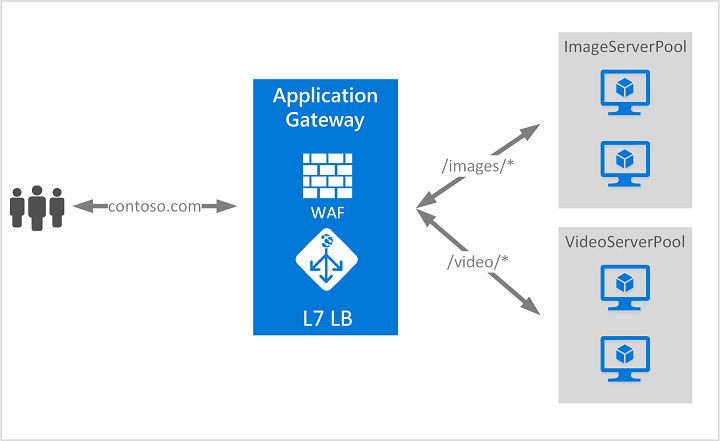
Application Gateway can do URL routing and more, for example, URI path or host headers. For example, if the incoming URL is /images then you can route the traffic to a specific set of servers, or if /video is in the URL, then the traffic can be routed to another set of servers. They can also make route decisions based on additional attributes of HTTP requests like host headers.
WAF provides protection against
- SQL-injection protection.
- Cross-site scripting protection.
- Protection against other common web attacks, such as command injection, HTTP request smuggling, HTTP response splitting, and remote file inclusion.
- Protection against HTTP protocol violations.
- Protection against HTTP protocol anomalies, such as missing host user-agent and accept headers.
- Protection against crawlers and scanners.
- Detection of common application misconfigurations (for example, Apache and IIS).
- Configurable request size limits with lower and upper bounds.
- Exclusion lists let you omit certain request attributes from a WAF evaluation. A common example is Active Directory-inserted tokens that are used for authentication or password fields.
- Create custom rules to suit the specific needs of your applications.
- Geo-filter traffic to allow or block certain countries/regions from gaining access to your applications.
- Protect your applications from bots with the bot mitigation ruleset.
- Inspect JSON and XML in the request body
Web Application Firewall has 2 operating modes.Detection mode & Prevention mode. Detection mode is used to monitor and load all threats, in this mode, WAF does not block any incoming requests. It's used to understand and learn from network traffic including identifying false positives. Please make sure that WAF logs are selected and turned on. Prevention Mode In this mode all threats are identified by the rules are blocked. The attacker receives a “403 unauthorized access” exception, and the connection is closed. Prevention mode records such attacks in the WAF logs.
An instance of Application Gateway can host up to 40 websites that are protected by a web application firewall. You can monitor attacks against your website by using real-time WAF logs which are integrated with Azure Monitor. An application gateway is also integrated with Azure Security Center.
Using Azure Portal Lets Create a Web Application Firewall on Application Gateway
We will log on to the Azure portal and create an Application Gateway with a Web Application Firewall.
Create Application Gateway & WAF
- Logon to azure portal
- Click on create resource, search select Application Gateway & click on create
- Enter a name & select a region
- Tier : select WAF ( WAF V2 Benefits include Autoscaling, Zone redundancy, Static VIP, Faster provisioning, Improved performance )
- Insance Count: 1
- Firewall status enabled
- Firewall Mode: detection ( for now )
- select or create a virutal network and click on OK
- click on next
- In the front end add a public ip
- backend: here you can add your virutal machines (The backend pool is used to route requests to the backend servers that serve the request. )
- configuration: here you can specify the front end backend and routing rules. Its in the routing rules you apply the ssl certificate
- review and create - click on save to create WAF On Application Gateway
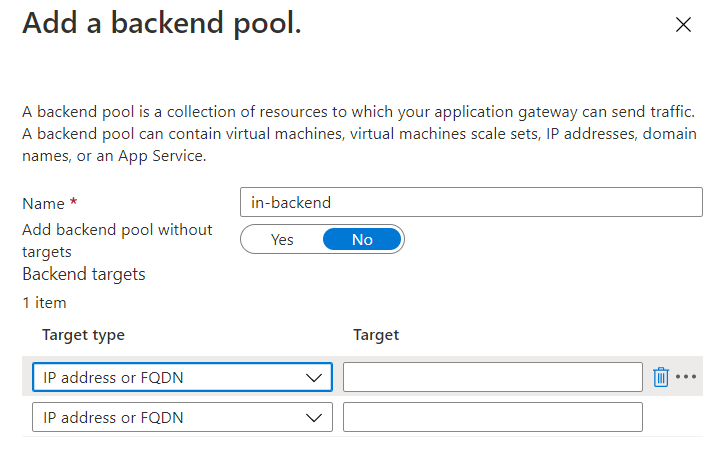
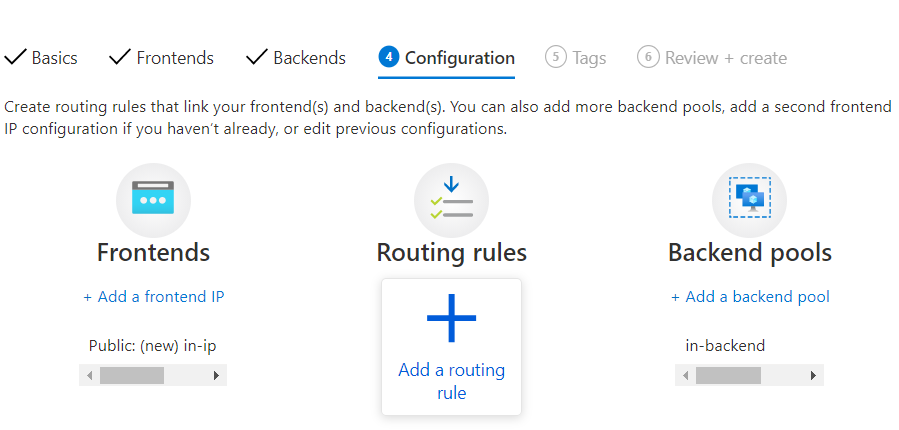
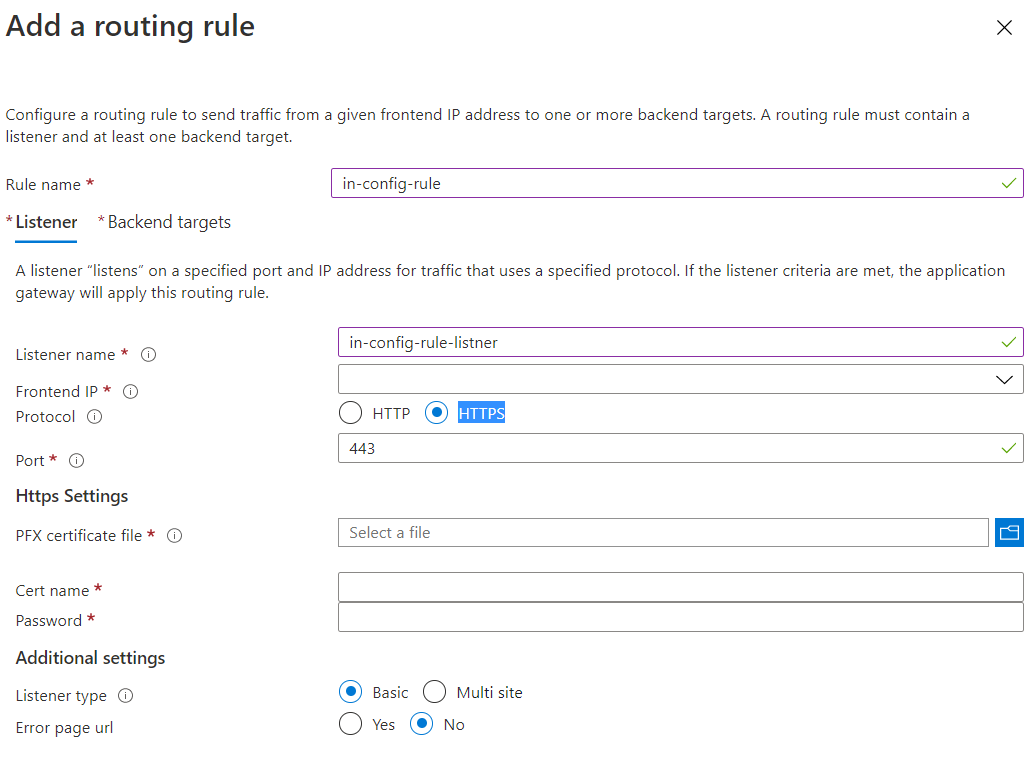
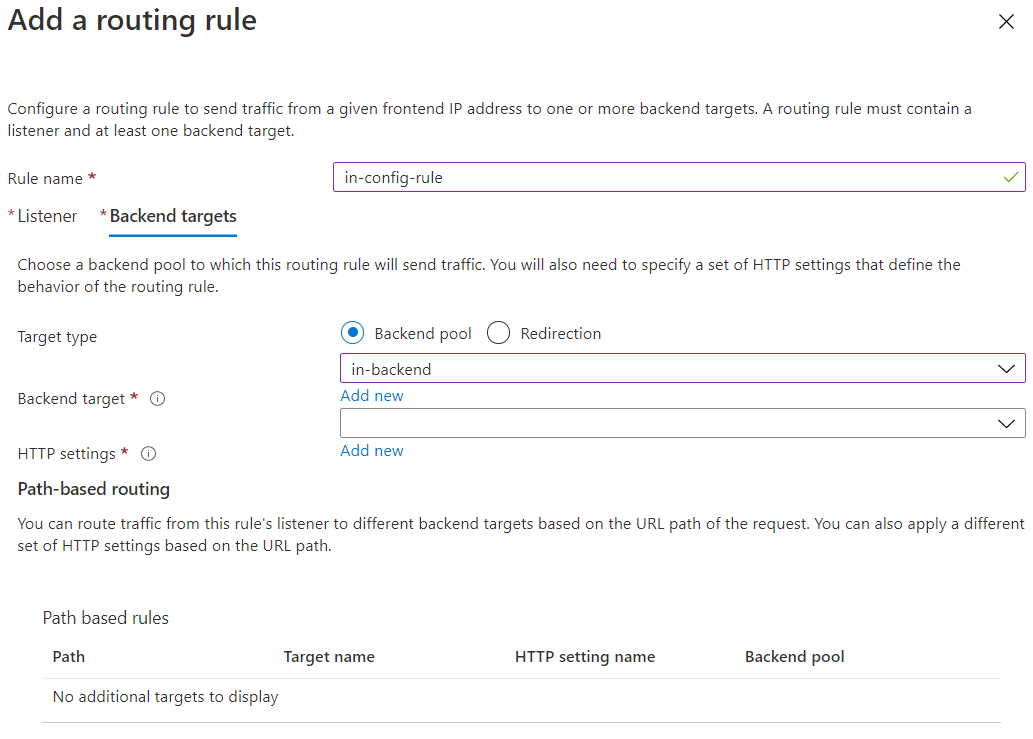
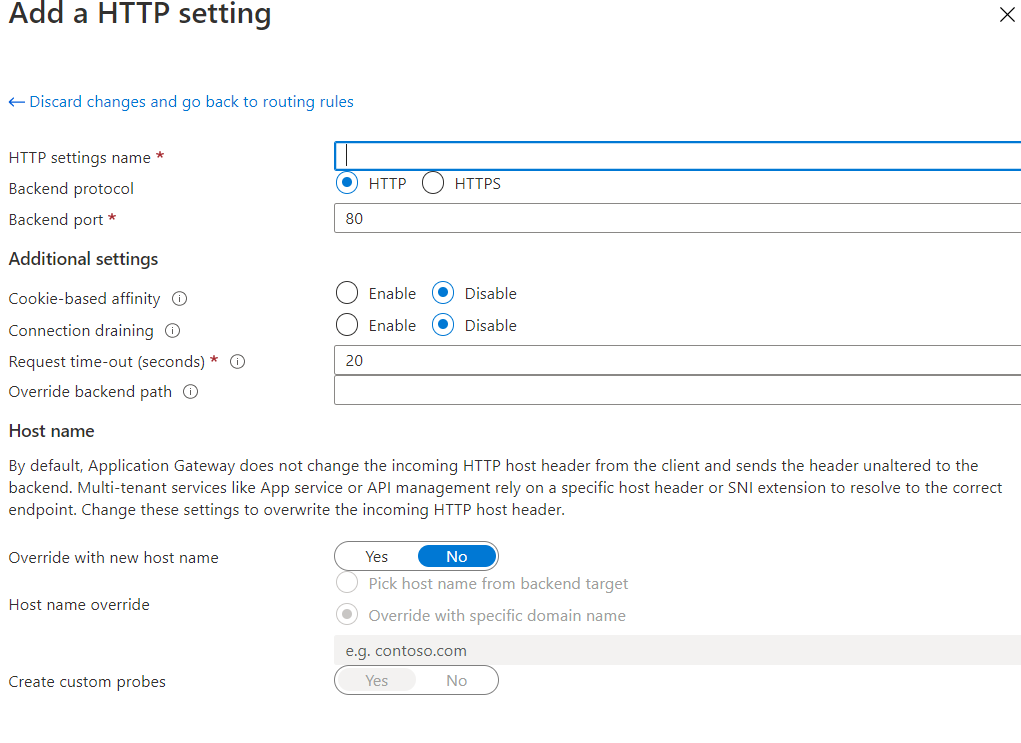
If you have already created an Application gateway, you can create a WAF and associate it with an application gateway.
Configure Diagnostics
We will use a storage account to store data for detection and prevention purposes. You could also use Azure Monitor logs or Event Hub to record data. Open application gateway under monitor select diagnostic settings. click on add diagnostic settings. On the destination, details select the archive to a storage account and select a storage account. enter a name for diagnostic settings and click on save.
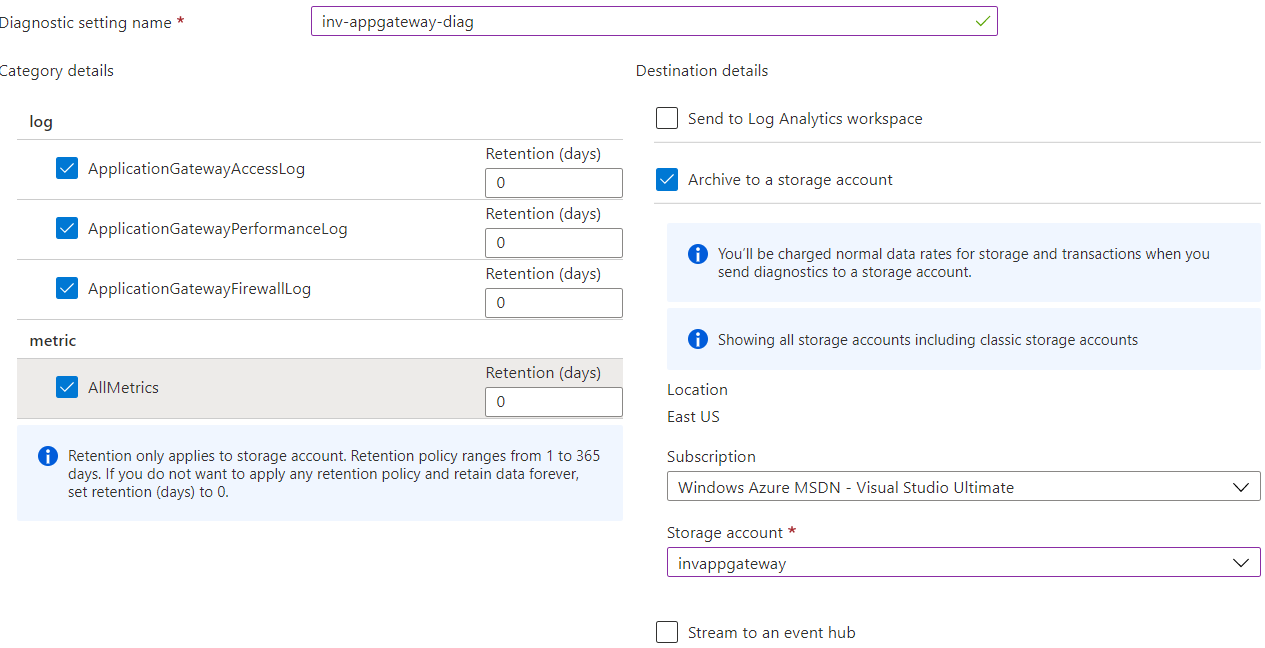
For the above, you can use an existing storage account or create a new one.
Create & Associate Web Application Firewall policies for Application Gateway
An instance of Application Gateway can host multiple websites that are protected by a web application firewall. If you want to protect all websites with a single policy with an application gateway. You can also create policies for individual websites. You can make as many policies as you want. Once you create a policy, it must be associated with an Application Gateway to go into effect, but it can be associated with any combination of Application Gateways and listeners. Once a Firewall Policy is associated to a WAF, there must always be a policy associated with that WAF. You may overwrite that policy, but disassociating a policy from the WAF entirely isn't supported.
To create a WAF policy On the upper left side of the portal, select Create a resource. Search for WAF, select Web Application Firewall, then select Create. On Create a WAF policy page, Basics tab, enter or select the following information, accept the defaults for the remaining settings, and then select Review create.
On the Association tab select Application Gateway and Associated Listner if you want to associate it with a listener
Testing To See If It works Fine
Go to Application Gateway. Go to overview. Copy the front end public Ip address and open it using your web browser. If everything works fine you would be able to see your website running.

